Penetration Testing as a Service
PTaaS powered by real penetration testing experts
Cutting-edge technology combined with expert hackers
Raxis employs highly skilled pentesters and advanced software to regularly monitor your system for any emerging threats. Our Penetration Testing services ensure the continuous viability of your security measures for maximum protection against potential breaches.
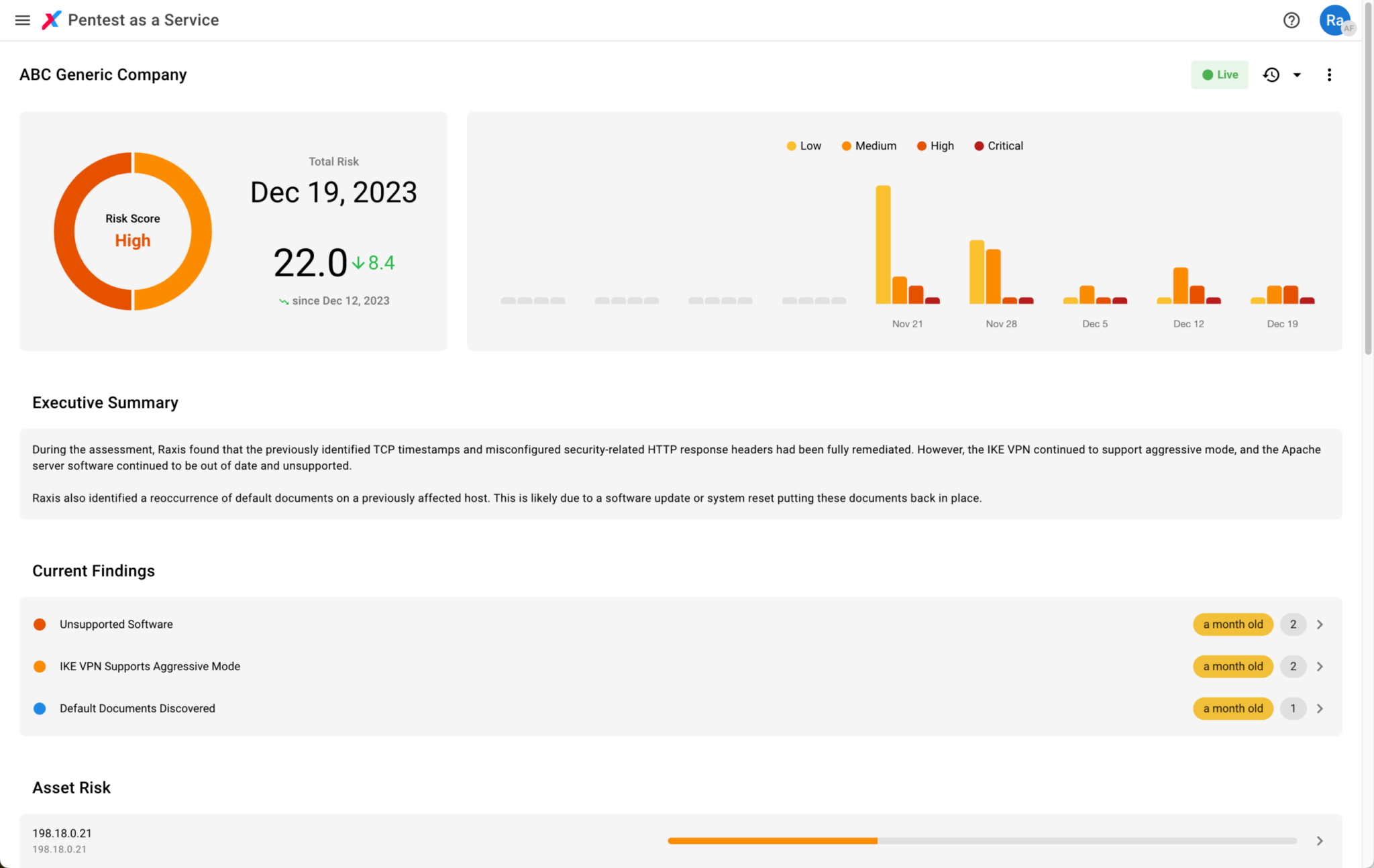
Powerful asset management
While PTaaS means Penetration Testing first, our managed pentest service also makes dealing with multiple systems and security vulnerabilities a little bit easier. Thanks to Raxis One, you’ll have a clear view of each security finding and details on how to resolve. Once you’ve remediated, you can kick off a retest to ensure the gaps are closed.
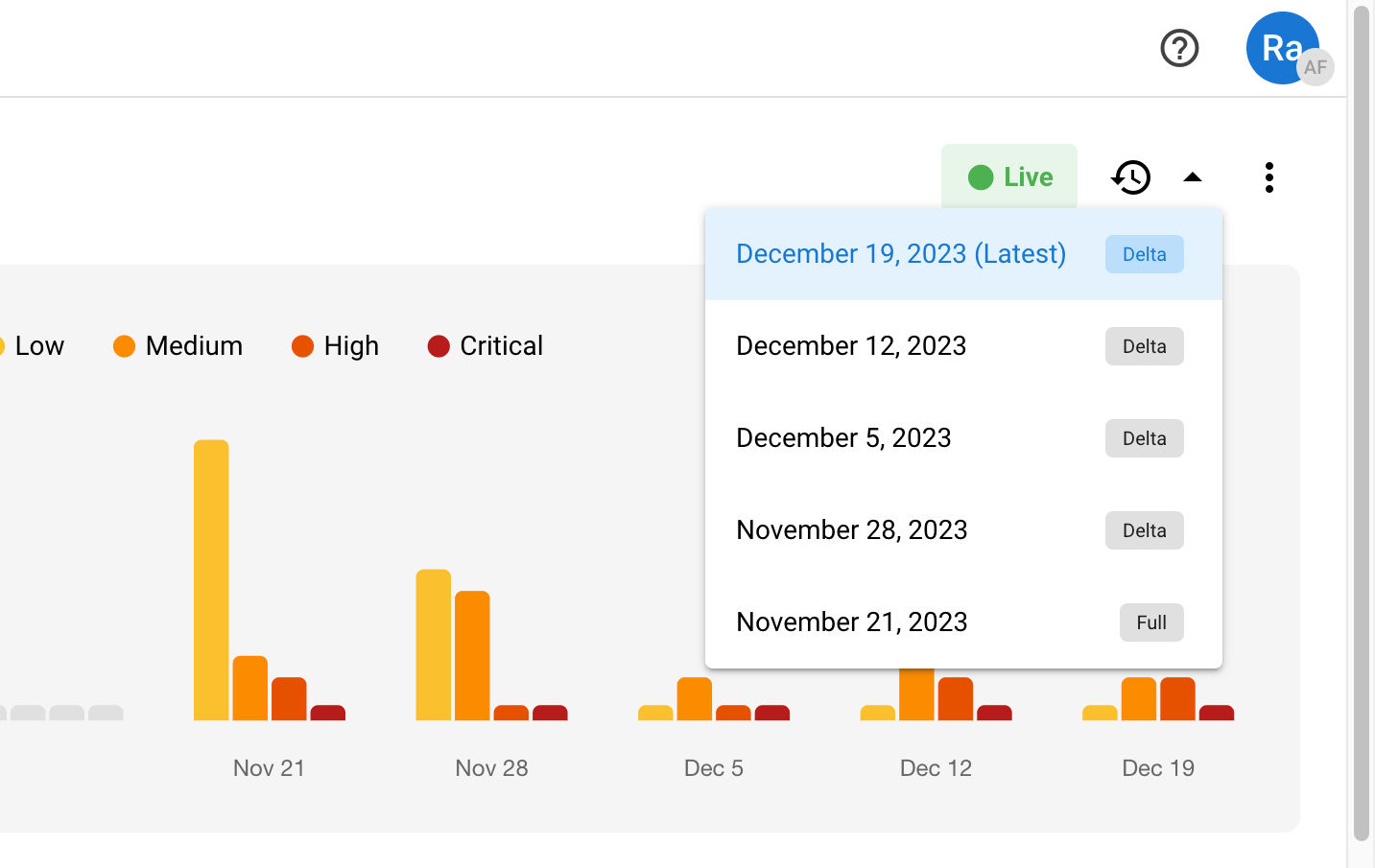
Time Travel helps you track progress
Using our Time Travel feature, Raxis One gives you a view of your security posture at any point in time you choose. This powerful tool provides a simple way to track changes in your environment over time.
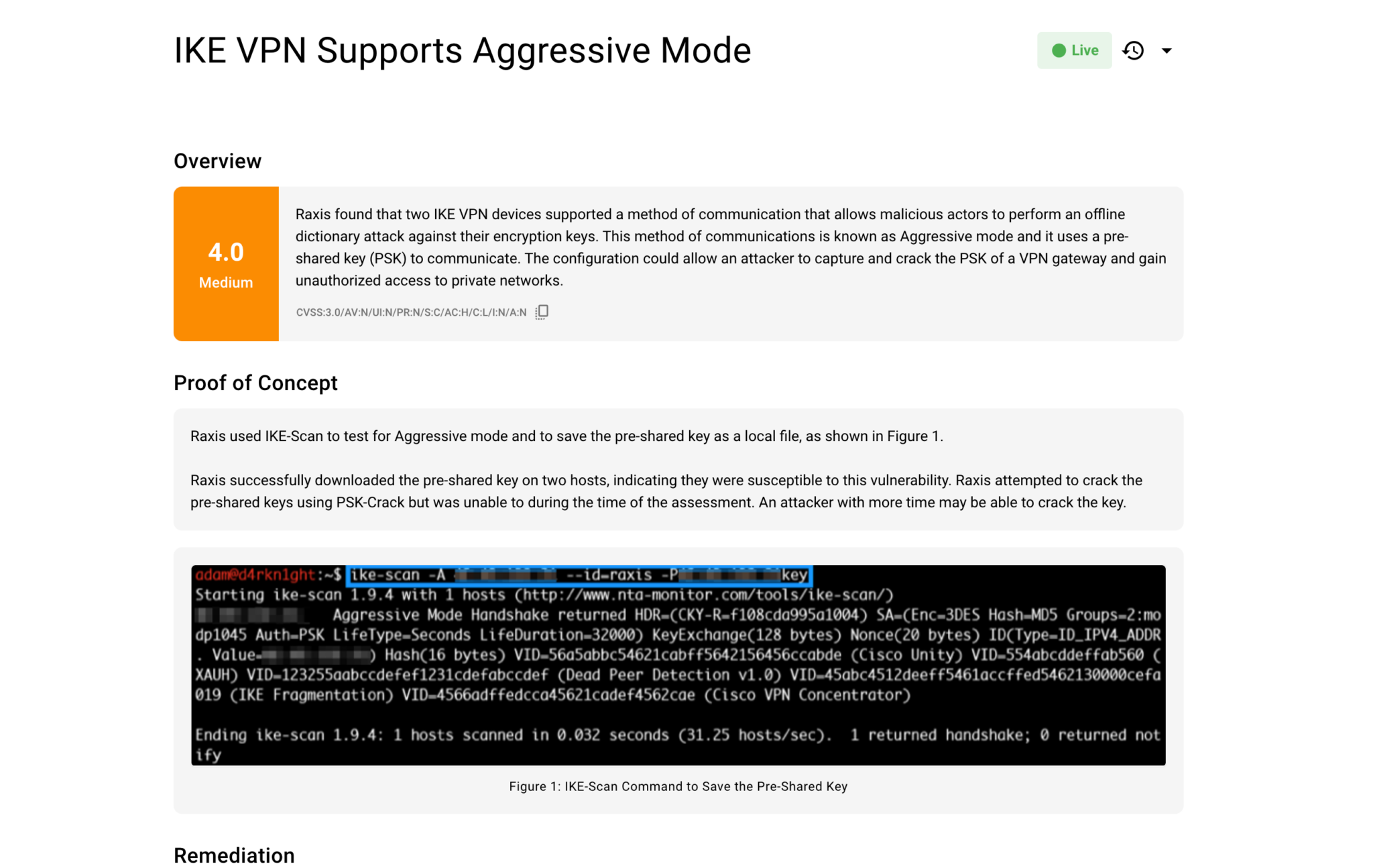
Penetration Testing, not re-branded scanning
When we set out to build a PTaaS or continuous pentest offering for Raxis, we had a lot of concerns around reducing quality and the impact that would have on our customers. Unlike many of our competitors, our solution remains audit approved as we make an attempt to exploit and provide a proof of concept as evidence.
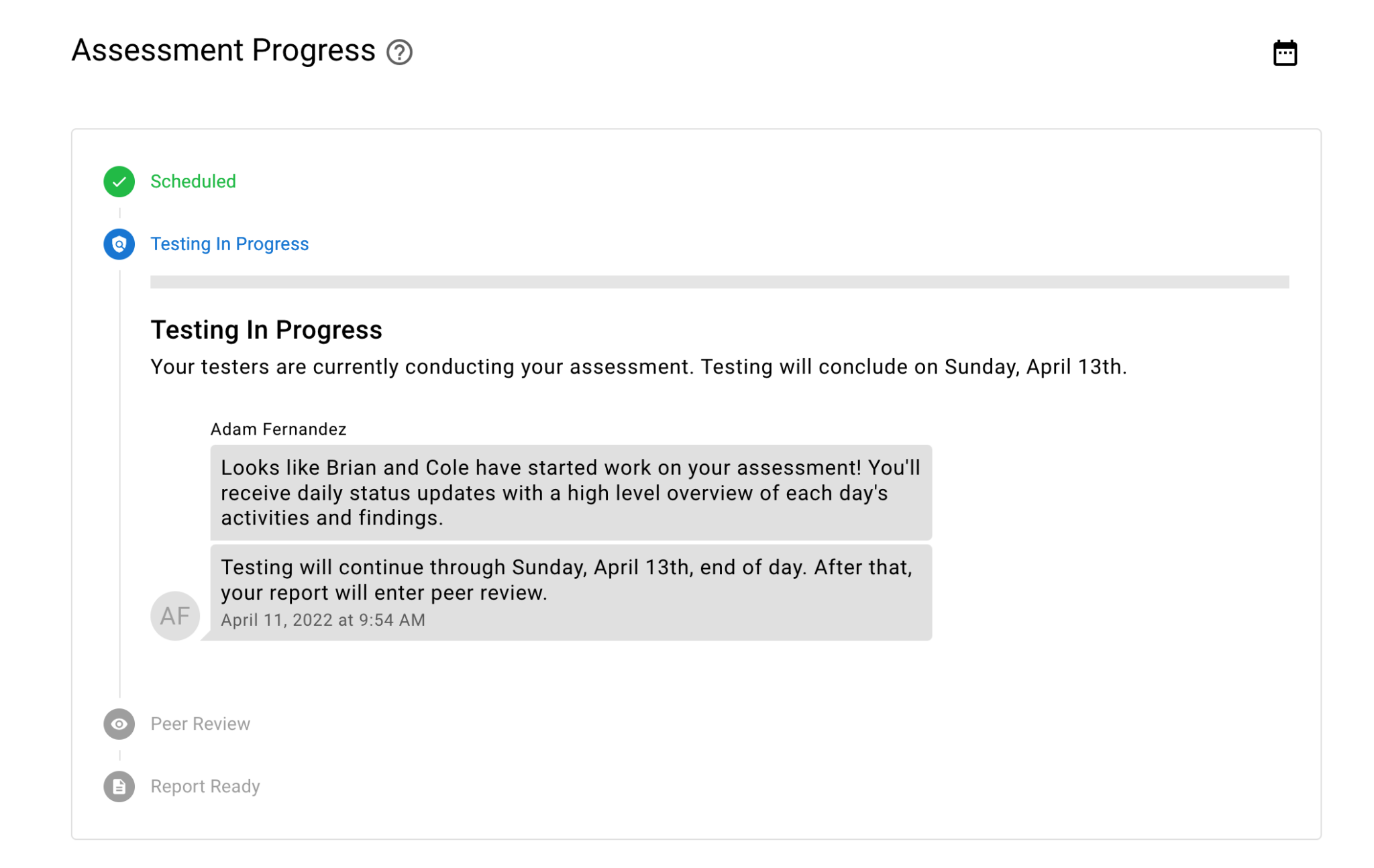
The secret is our engineers
Through the power of Raxis One scanning, our system keeps an eye out to identify possible cybersecurity vulnerabilities. If something is found, Raxis penetration testing engineers step in to determine viability of the new issue, map an exploit plan, and make an attempt to breach your systems.
Continuous Protection with PTaaS
Secure Your Business
Protect your business from potential cyber attacks with regular penetration testing services.
Identify Vulnerabilities
Uncover weaknesses in your security measures and take proactive steps to strengthen your defenses.
Demonstrate Compliance
Demonstrate your commitment to security and regulatory compliance with regular penetration tests.

Protect Your Data
Keep your sensitive data safe from potential hackers with a comprehensive penetration testing approach.
Strengthen Your Defenses
Gain valuable insights into your security infrastructure and improve your overall defense strategies.
Stay Ahead of Threats
Stay one step ahead of potential cyber threats with a regularly scheduled penetration testing service.
Two options to fit your needs
PTaaS supports automatic or manual scheduling of real Penetration Testing using our elite ethical hacking team.
On Demand
Maybe you’ve just wrapped up some coding, or maybe you’re just really concerned about the current threat environment. Whatever the reason, you can kick off a Penetration Test whenever you’d like. We’ll get it started with detailed vulnerability scanning within 1 business day and schedule our engineer to start a real penetration test.
Continuous
Using state-of-the-art scanning technology, we perform frequent scanning of your environment to ensure we don’t miss any emerging threats. We’ll evaluate your ongoing scans with the prior pentest report to ensure that nothing new has become a problem. In the event there is a new threat, our engineers are automatically scheduled to perform a penetration test.
Types of Service Provided
Securely test your business’s networks, applications, and APIs with Raxis PTaaS. Our experienced team offers a wide range of testing options and provides detailed reports to help protect sensitive data.
External Network Penetration Test
Raxis takes a close look at your internet facing systems (including cloud hosted) and utilizes our hacking skills in an attempt to safely breach your network perimeter.
Available as Continuous or On-Demand PTaaS
Internal Network Penetration Test
Internal Network PTaaS simulates the impact of a malicious insider using a real human penetration testing engineer.
Available as Continuous or On-Demand PTaaS
Web Application Penetration Test
Much like our traditional web app penetration testing model, Raxis leaves no stone unturned as we examine each user role, input field, and session cookie.
Available as On-Demand PTaaS
API Penetration Testing
Raxis scrutinizes each API call for anomalies through direct interaction and by manipulating application data in flight by manually interacting with advanced testing tools.
Available as On-Demand PTaaS
F.A.Q.
Frequently Asked Questions
Raxis PTaaS, or Penetration Testing as a Service, combines the speed and accuracy of security scanning tools and real human powered Penetration Testing. Raxis uses state of the art automated vulnerability scans, powered by Tenable, to watch for changes and new risks from emerging threats. If something is detected, we move quickly to perform an analysis of the potential findings and subsequently a real penetration test, allowing you to focus on business while we keep an eye on your cybersecurity risk. Raxis One provides a way to check on your security posture at any time, as well as the ability to communicate in near real-time with our penetration testing engineers.
At Raxis, our Pentest as a Service (PTaaS) goes beyond a simple scan. We offer a complete range of Penetration Testing services utilizing our experienced team and state-of-the-art software. Our thorough report not only includes detailed screenshots, but also provides step-by-step remediation guidance for each identified issue. On top of that, we conduct retesting and validation to ensure your complete protection. Rest assured, Raxis PTaaS delivers much more than just a standard Pentest – it’s a comprehensive solution.
On Demand Penetration Testing is an excellent fit for organizations that are making frequent changes to their applications or network environment. By skipping the procurement process, onboarding penetration testers, and frequent kick off calls, PTaaS On Demand provides a fast way to start a Penetration Test powered by the Raxis team of professional hackers. The Raxis team will work closely with your development or network teams to help resolve security findings in near real-time, giving you a real advantage in speed to market and reduced security risk.
When it comes to keeping your company secure, it is important to establish a strong base. We acknowledge that each company has its own unique operations and may feel confident in their current security measures. Therefore, if our team discovers any weaknesses during our Penetration Testing, we will collaborate closely with you to address them and identify the most effective solutions that cater to your business needs. Additionally, we value the importance of time, which is why we offer the option to oversee these issues through our PTaaS service, saving you time and effort. With Raxis, you can rely on our unwavering dedication to safeguarding your company. Always remember, we are here to assist in whatever manner you prefer.
With continuous pentesting, our team conducts frequent scans to monitor your system for any changes. We carefully look for new elements that may have emerged since our last analysis. If we find something noteworthy, we will carry out another Penetration Test to thoroughly examine this potential new attack vector. This updated information will be reflected in your Raxis One report, which will also include recommendations on how to address our findings. This process will be repeated every time we discover a new potential attack vector. As for on-demand pentesting, where you have the option to initiate a new penetration test, there are certain limitations. You are able to select the number of on-demand tests you would like per year. These tests will only be conducted upon your request and will include a full pentest, report, and retesting when you are ready.
Yes. PTaaS is real penetration testing, so it meets or exceeds all penetration testing standards. This includes (but is not limited to) compliance with NIST 800-53, NIST 800-171/CMMC, PCI, HIPAA, GLBA, ISO 27001, and SOX. Our team at Raxis ensures that all of our services adhere to these standards and go above and beyond to provide top-of-the-line security for our clients. Our commitment to compliance and excellence sets us apart as a leader in the industry, giving you peace of mind and confidence in our services. Let us show you how Raxis can help you achieve your cybersecurity goals.
At Raxis, our ethical and legal standards are of utmost importance to us. This is demonstrated through our use of clear and comprehensive contracts that set forth the parameters of our work. As part of our commitment to upholding these values, we adhere to a strict policy prohibiting any harm or destruction of our clients’ property. Our primary objective is not to cause damage, but rather to uncover vulnerabilities that real hackers could exploit. In addition, we offer valuable insights and imparting education to our customers, empowering them to preemptively safeguard against cyber attacks. Our agreements have the full knowledge and endorsement of company leadership, solidifying transparency and consent. Above all, we operate with honesty and always prioritize the well-being and safety of our valued clients.
As a penetration tester, it is crucial for us to follow strict protocols and protocols. Our primary goal is to keep the system up and running and safeguard the integrity of its data. Unlike malicious hackers, we prioritize avoiding any real harm. Moreover, when gathering evidence of access, we take additional precautions to conceal any confidential information. While we adhere to our clients’ parameters and regulations, we also aim to push the boundaries and challenge the effectiveness of their security protocols.
With Raxis PTaaS, we take great pride in our comprehensive approach to conducting penetration tests. After carefully assessing the project, we collaborate closely with cloud providers to ensure they are aware of our actions. Our team of highly skilled professionals has conducted numerous tests on a variety of platforms, including Amazon AWS/EC2, Microsoft Azure, Google Cloud, Rackspace, and VMWare Cloud. We have also gained extensive experience working with widely used content delivery front ends such as CloudFlare and Akamai. Regardless of our clients’ technology stack, Raxis is committed to utilizing the most effective methods to meet their specific penetration testing needs. Our detailed reports offer valuable insights and recommendations for enhancing overall security measures.
Password cracking is a vital component of Raxis’ comprehensive and meticulous penetration testing service. Our PTaaS team employs sophisticated methodologies and cutting-edge tools to evaluate the effectiveness of your organization’s password policy and the level of its execution. Additionally, our adept personnel can leverage previously compromised passwords to gain unauthorized access to other systems, enhancing the authenticity of a simulated data breach. Raxis employs robust encryption methods to safeguard all hash data, both in transit and at rest, to ensure maximum security. As part of our unyielding commitment to confidentiality and protection, after the password cracking process is finalized, we ensure the secure erasure of all password hashes. We provide a comprehensive analysis of our findings, including details on password robustness, intricacy, and examination, as part of a redacted pentest report.
Specifications
PTaaS
- PTaaS services are highly customizable, as every customer is unique
- Powered by Raxis One, a secure web interface for all Raxis services
- Fully capable of working with cloud providers and content delivery networks such as Amazon AWS, Microsoft Azure, Google Cloud, Cloudflare, Akamai, hybrid cloud, and SaaS solutions
- Utilizes the same tools and techniques as a blackhat hacker
- Exploitation, pivoting to other in-scope systems, and data exfiltration in scope
- Executive debrief conference provided, if desired
- Optional re-test to validate remediation
- Continuous and/or On-Demand Penetration Testing
- Based on the MITRE ATT&CK penetration testing framework
- Meets or exceeds requirements for NIST 800-171/CMMC, PCI, HIPAA, GLBA, ISO 27001, and SOX

